Types Of Phishing Attacks
Phishing attacks are a prevalent and insidious form of cyber threat, posing a significant risk to individuals, businesses, and organizations worldwide. These attacks, designed to deceive and manipulate victims into revealing sensitive information or performing actions that compromise their security, have evolved into various sophisticated forms. Understanding the different types of phishing attacks is crucial for implementing effective preventive measures and maintaining a robust cybersecurity posture.
The Evolution of Phishing Attacks

The history of phishing attacks can be traced back to the early days of the internet, with the first recorded incident occurring in the late 1990s. Since then, these attacks have undergone a remarkable transformation, adapting to the ever-changing digital landscape and user behavior. From the initial, relatively crude attempts to more sophisticated and targeted campaigns, phishing has become a highly effective tool in the arsenal of cybercriminals.
Common Types of Phishing Attacks

Phishing attacks come in various forms, each with its own unique characteristics and methods. Here’s an overview of some of the most common types:
1. Email Phishing
Email phishing is the most prevalent and well-known form of phishing. Attackers send deceptive emails that appear to be from legitimate sources, such as banks, government institutions, or popular online services. These emails often contain malicious links or attachments that, when clicked, can lead to the installation of malware or the disclosure of sensitive information.
For instance, a phishing email might impersonate a well-known online retailer, asking the recipient to "update their payment details" by clicking on a link. This link could direct them to a fake website designed to steal their login credentials or credit card information.
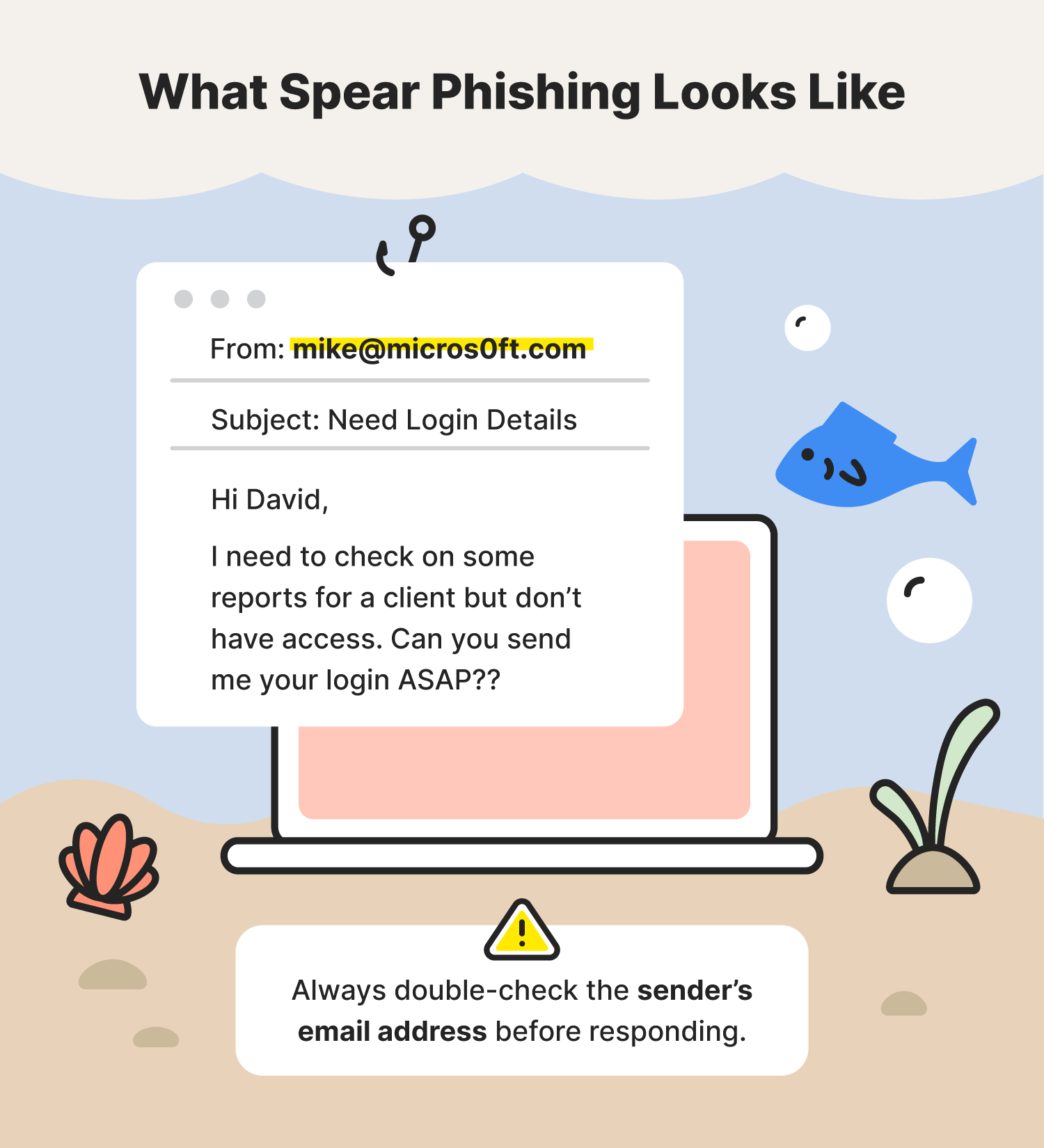
2. Spear Phishing
Spear phishing is a highly targeted form of phishing attack. Unlike generic phishing emails, which are sent to a large number of recipients, spear phishing emails are tailored to specific individuals or organizations. These attacks often leverage personal or professional information to make the email appear more credible and increase the chances of success.
A common example of spear phishing involves an attacker posing as a colleague or superior, requesting sensitive information or urging the recipient to take urgent action. The success of these attacks often relies on the attacker's ability to gather and utilize personal details effectively.
3. Whaling
Whaling is a sophisticated form of spear phishing that specifically targets high-profile individuals within an organization, such as CEOs, CFOs, or other C-level executives. These attacks are meticulously planned and executed, with the aim of extracting valuable corporate data or financial assets.
Whaling emails are carefully crafted to appear as legitimate business communications, often using official-looking logos and language. The content may include urgent requests for financial transactions or sensitive information, leveraging the target's position and authority within the organization.
4. Smishing (SMS Phishing)
Smishing, or SMS phishing, is a phishing attack conducted through text messages. Attackers send SMS messages to mobile phone users, often with a sense of urgency or an enticing offer. These messages typically contain a link or a phone number that, when clicked or called, leads to a phishing website or a voice phishing scam.
For example, a smishing message might claim to be from a courier service, stating that there's an issue with a package delivery and providing a link to "resolve the issue." Clicking the link could lead to a fake website designed to steal personal or financial information.
5. Vishing (Voice Phishing)
Vishing, or voice phishing, involves using telephone calls to deceive victims. Attackers often pose as representatives from legitimate organizations, such as banks or government agencies, and attempt to trick victims into providing sensitive information over the phone.
A common vishing scenario involves an attacker pretending to be a bank employee, calling a victim and claiming that their account has been compromised. The attacker then requests the victim's account details and personal information to "verify their identity" and "resolve the issue."
6. Pharming
Pharming is a more advanced and complex form of phishing. Instead of relying on social engineering to trick victims into visiting a fake website, pharming attacks manipulate the Domain Name System (DNS) to redirect users to a malicious website, even when they enter the correct URL.
This can be achieved by infecting a victim's computer with malware that alters the DNS settings, causing legitimate website requests to be redirected to phishing sites. Pharming attacks can be particularly challenging to detect and prevent.
7. Clone Phishing
Clone phishing involves creating an exact replica of a legitimate and previously delivered email, often containing an attachment or a link. The attacker then replaces the original link or attachment with a malicious one and resends the email, hoping that the recipient will be less cautious since they recognize the email as legitimate.
For instance, an attacker might intercept an email containing an invoice from a legitimate company and replace the invoice link with a malicious one. When the recipient clicks the link, they are directed to a phishing site designed to steal their payment information.
Technical Specifications and Performance Analysis
Phishing attacks employ various technical means to achieve their objectives. Here’s a breakdown of some key technical aspects:
1. Social Engineering
Social engineering is a critical component of phishing attacks. Attackers leverage psychological manipulation to trick victims into making security-compromising decisions. This can involve creating a sense of urgency, fear, or curiosity, prompting victims to act without fully considering the potential risks.
2. Malicious Links and Attachments
Phishing emails often contain malicious links or attachments. These can lead to the installation of malware, such as keyloggers, which can capture sensitive information like login credentials or credit card details. Attachments may also contain malicious macros or scripts that execute when opened, compromising the victim’s system.
3. Domain Spoofing
Domain spoofing is a technique used in phishing attacks to make a fake website or email appear legitimate. Attackers register domain names that are similar to well-known brands or organizations, often with subtle misspellings or character substitutions. This makes it difficult for victims to distinguish between the real and fake domains.
4. HTTPS and SSL Certificates
To make their phishing websites appear more trustworthy, attackers sometimes use HTTPS and SSL certificates. These security protocols, indicated by a padlock icon in the browser’s address bar, are typically associated with secure websites. However, in phishing attacks, these indicators can be misleading, as the certificates may be self-signed or obtained through fraudulent means.
5. Email Spoofing
Email spoofing involves forging the sender’s email address to make it appear as if the email is coming from a legitimate source. This technique is commonly used in phishing attacks to deceive recipients into believing that the email is from a trusted sender, increasing the likelihood of them taking the desired action.
Comparative Analysis and Real-World Examples
To illustrate the impact and effectiveness of different phishing attack types, let’s examine some real-world examples:
1. Business Email Compromise (BEC)
In a BEC attack, a high-profile executive’s email account is compromised, often through spear phishing. The attacker then uses the compromised account to send fraudulent emails to employees or business partners, requesting urgent wire transfers or sensitive information. This type of attack has resulted in significant financial losses for businesses.
2. CEO Fraud
CEO fraud is a form of whaling attack where the attacker impersonates a company’s CEO or another high-ranking executive. The attacker sends emails or makes phone calls to employees, often using a sense of urgency, to request wire transfers or sensitive information. This type of attack has led to substantial financial losses and reputational damage for organizations.
3. Online Banking Phishing
Online banking phishing attacks target individuals with emails or text messages claiming to be from their bank. These messages often contain links to fake login pages designed to steal login credentials. Once the attacker has the victim’s login information, they can gain access to their online banking account and potentially transfer funds or steal personal data.
Future Implications and Mitigation Strategies

As phishing attacks continue to evolve and become more sophisticated, it’s crucial to stay vigilant and implement effective mitigation strategies. Here are some key considerations for the future:
1. Advanced Authentication Methods
Implementing advanced authentication methods, such as multi-factor authentication (MFA) or biometric authentication, can significantly enhance security. These methods add an extra layer of protection, making it more difficult for attackers to gain unauthorized access to accounts, even if they have stolen login credentials.
2. User Education and Awareness
One of the most effective defenses against phishing attacks is user education. By training employees and individuals to recognize the signs of phishing attempts, organizations can create a culture of cybersecurity awareness. Regular training sessions, simulated phishing tests, and clear reporting protocols can help identify and mitigate potential threats.
3. AI and Machine Learning
Artificial intelligence (AI) and machine learning (ML) technologies are increasingly being used to detect and prevent phishing attacks. These technologies can analyze vast amounts of data, identify patterns, and flag potential threats in real-time. AI-powered email filters and security solutions can help identify and block phishing emails before they reach their intended targets.
4. Continuous Monitoring and Incident Response
Establishing a robust incident response plan is crucial for mitigating the impact of successful phishing attacks. This involves continuously monitoring networks and systems for signs of compromise, implementing robust backup and recovery strategies, and having a well-defined plan for responding to and containing any security incidents.
5. Collaboration and Information Sharing
Phishing attacks are a global threat, and collaboration between organizations, governments, and cybersecurity professionals is essential for effective defense. Sharing threat intelligence, best practices, and incident response strategies can help the community as a whole stay ahead of evolving phishing tactics.
💡 While phishing attacks are a significant concern, staying informed and implementing robust security measures can significantly reduce the risk of falling victim to these threats. Regularly updating security protocols, staying vigilant, and fostering a culture of cybersecurity awareness are key to maintaining a strong defense against phishing and other cyber threats.
How can I recognize a phishing email or text message?
+Phishing emails often have subtle clues that can help you identify them. Look for spelling and grammar errors, generic greetings, urgent or threatening language, and unexpected requests for personal information. Additionally, hover over links to check the URL before clicking, and be cautious of attachments, especially if they are unexpected or have unusual file extensions.
What should I do if I receive a suspicious email or text message?
+If you receive a suspicious email or text message, it’s important to remain calm and not click on any links or download any attachments. Instead, contact the alleged sender through a trusted channel, such as a phone call or a separate email, to verify the legitimacy of the message. If you suspect a phishing attempt, report it to your organization’s IT or security team immediately.
How can I protect myself from phishing attacks on social media platforms?
+Social media platforms can be a breeding ground for phishing attacks. To protect yourself, be cautious of messages or posts that ask for personal information or urge you to click on links. Verify the authenticity of the sender or poster by checking their profile and interacting with them directly. Additionally, enable two-factor authentication (2FA) on your social media accounts to add an extra layer of security.

